As Nigeria accelerates its digital transformation journey, the country faces a critical juncture in securing its e-governance infrastructure. The 2025 Nigeria Cybersecurity Outlook by Deloitte reveals a stark reality: cyberattacks are no longer a question of “if” but “when,” with even cyber-mature organizations globally reporting 11 or more cybersecurity incidents annually. This represents a 7% increase from 2023. For Nigerian policymakers, this represents both a critical challenge and an opportunity to build resilient e-governance infrastructure that can withstand the evolving threat landscape.
Nigeria’s Cybersecurity Reality Check
The current state of Nigeria’s digital security presents a complex picture of progress and vulnerability.
While the country has made significant strides in digitizing government services, the underlying cybersecurity infrastructure remains fragmented and inadequately protected.
A recent research published in the Journal of Science Technology and Education (2025) by Dako et al. examined Nigeria’s cybersecurity in e-governance. Using a mixed-method approach, the researchers surveyed 54 IT professionals, government officials and cybersecurity experts across Nigeria. They conducted 15 interviews and organized focus groups. The study found that 72% of respondents saw outdated legacy systems as major cybersecurity risks. 74% flagged inconsistent multi-platform security, and 78% identified IoT devices as highly vulnerable. At the same time, 85% emphasized AI’s role in threat detection. Incident response strategies were rated only moderately effective.
These risks are compounded by what Deloitte identifies as the “Japa syndrome”, or a critical brain drain where cybersecurity professionals are leaving the country for better opportunities abroad. This talent exodus has left businesses and government agencies scrambling to find skilled professionals to secure their operations against increasingly sophisticated threats.
The situation is further complicated by economic pressures driving organizations to seek cost-effective, locally-sourced cybersecurity solutions. While this shift toward indigenous security tools presents opportunities for local innovation, it also carries inherent risks. Many of these rapidly developed solutions lack rigorous testing and comprehensive threat intelligence, potentially introducing new vulnerabilities into already strained security infrastructures.
The AI Arms Race: Defense vs. Attack
2024 marked a pivotal shift in the global cybersecurity landscape, with artificial intelligence becoming both the ultimate weapon and shield in cyber warfare. As Tope Aladenusi and Funmilola Odumuboni noted in the 2025 outlook, “AI-powered attacks are making cyber threats more sophisticated, automated, and precise.” This dual-use nature of AI creates a paradox that Nigerian e-governance systems must navigate carefully.
On the defensive side, AI-powered tools are enhancing threat detection, automating incident response and analyzing patterns to identify risks early. These capabilities enable government systems to respond quickly and effectively to emerging threats. However, the same technology is empowering cybercriminals to automate phishing campaigns, create polymorphic malware that evades detection and craft hyper-realistic deepfakes that can deceive even sophisticated security systems.
For Nigeria’s e-governance framework, this means that traditional security approaches are no longer sufficient. This implies that government agencies must embrace AI not merely as a defensive tool but as an integral component of a comprehensive cybersecurity strategy that can evolve with the threat landscape.
The Third-Party Risk Epidemic
One of the most concerning trends identified in the 2025 outlook is the escalation of third-party risks. As Nigeria’s digital economy expands and government services increasingly rely on cloud-based solutions—including financial applications, HR platforms and document-signing tools—cybercriminals are targeting the weakest links in these interconnected supply chains.
Also, the proliferation of Application Programming Interfaces (APIs), while critical for seamless government service integration, introduces new vulnerabilities. Poorly secured APIs can serve as entry points for attackers, and the interconnected nature of these systems means a single compromised integration can have cascading effects across multiple government platforms.
Current data shows that only 30% of government officials believe security policies are well-coordinated across different platforms. This represents a critical vulnerability that third-party attackers actively exploit. This fragmentation makes it difficult to maintain consistent security standards and creates blind spots that malicious actors can leverage.

The Growing Menace of Identity Theft
The Nigeria Inter-Bank Settlement System (NIBSS) report from 2024 documented notable incidents involving fraudsters using social engineering techniques to gain unauthorized access to sensitive information and successfully perform account takeovers. As digital transformation accelerates, these identity theft and fraud cases are becoming increasingly pervasive, raising serious concerns for both government operations and citizen trust.
The rapid adoption of digital payment systems and mobile banking in government services has created new attack vectors that cybercriminals are actively exploiting. With many government agencies still enhancing their security infrastructure, criminals are finding innovative ways to exploit system weaknesses and gain access to citizens’ personal and financial information.
Learning from Global Leaders
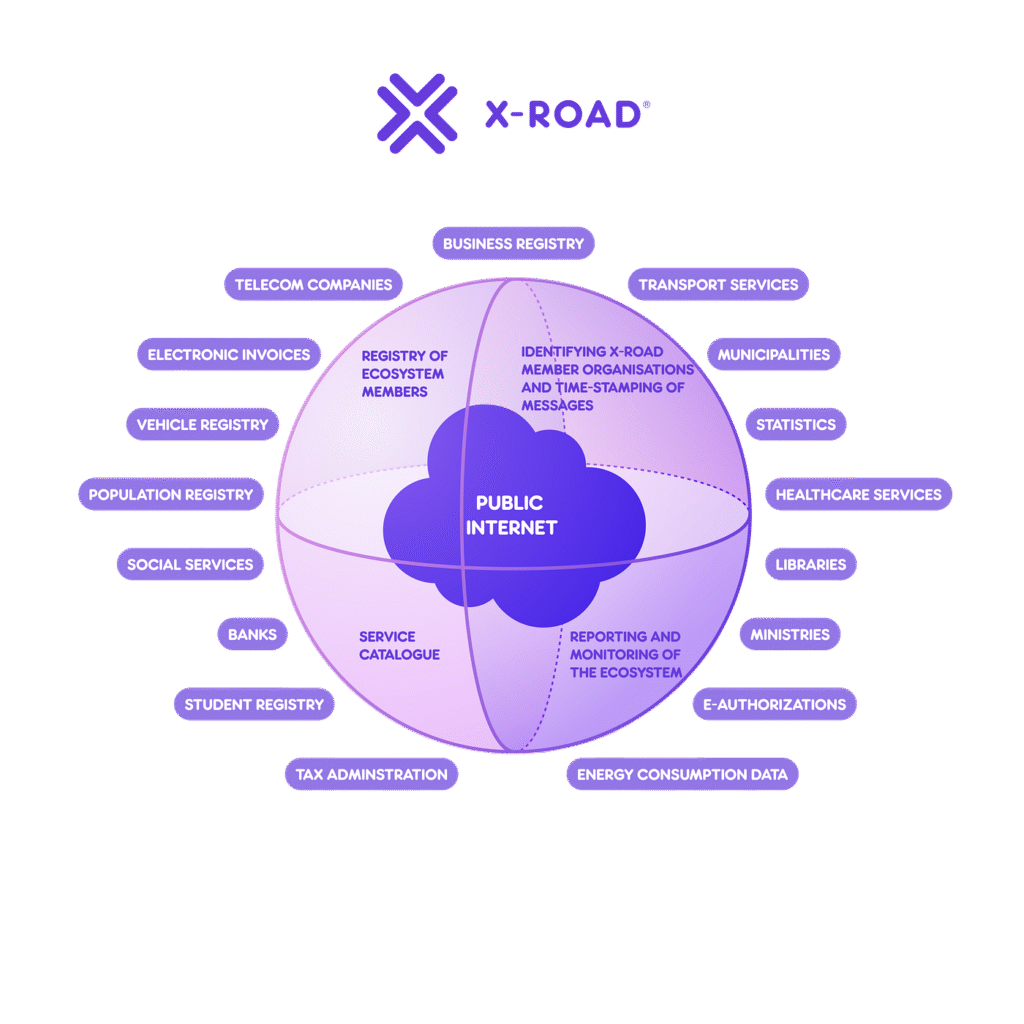
Estonia’s experience offers valuable insights for Nigeria. The Nordic country has successfully implemented a comprehensive digital government ecosystem protected by the X-Road framework. The X-Road framework is an open-source secure data exchange infrastructure that connects various government databases while maintaining strict security protocols. Estonia’s approach demonstrates that robust cybersecurity and seamless digital services can coexist when properly architected.
Similarly, countries like South Korea and Israel have shown that strategic cybersecurity governance, combined with adaptive risk management, can create resilient digital government ecosystems. These nations have invested heavily in AI-driven threat detection systems and established clear protocols for incident response. And these measures have proven effective in protecting critical infrastructure.
The key lesson from these success stories is that cybersecurity cannot be an afterthought in e-governance implementation. It must be built into the foundation of digital government services from the ground up.
Building the Three-Pillar Framework
Based on extensive research and analysis of global best practices, Nigeria requires a comprehensive cybersecurity framework built on three foundational pillars:
1. Adaptive Risk Management with Local Context
Nigeria needs a risk management approach that can evolve with the country’s unique threat landscape and resource constraints. The MARISMA methodology offers a model for continuous, context-aware risk analysis that can be adapted to Nigeria’s governmental structure.
This approach involves creating dynamic risk catalougs that can be updated without overhauling entire methodologies that are particularly important given the economic pressures organizations face in 2025.
As the Deloitte outlook emphasizes, “The key to navigating the cybersecurity landscape lies in striking a delicate balance between innovation, cost-efficiency, and robust security.”
Nigerian agencies should develop standardized risk patterns that can be customized for different sectors while maintaining consistency across government operations. This approach must account for the reality that indigenous security tool developers, while offering tailored solutions, often prioritize rapid deployment over rigorous testing.
2. Secure Interoperability Infrastructure
The coordination challenge identified in current research, where 74% of cybersecurity professionals note inconsistent security measures as a major vulnerability, requires a centralized approach to interoperability. A framework similar to Estonia’s X-Road system could provide the secure data exchange layer that Nigeria’s e-governance ecosystem desperately needs.
Such a system would enable seamless service delivery while ensuring citizen data protection across all government interactions. This is particularly crucial as the 2025 outlook predicts continued growth in cloud-based government solutions and API integrations, both of which require robust security frameworks to prevent the third-party risks that have plagued other nations.
3. Strategic Cybersecurity Governance and Talent Development
The talent shortage crisis highlighted in the 2025 outlook requires innovative approaches to building and retaining cybersecurity expertise. Forward-thinking government agencies must invest in local capacity-building initiatives, including cybersecurity training programs, partnerships with universities, and in-house mentorship schemes.
In sum, Nigeria needs a governance framework that defines clear roles and responsibilities, establishes regular training programs, and creates mechanisms for continuous monitoring and improvement. This includes developing incident response capabilities that can quickly contain and remediate security breaches. The Nigeria Data Protection Commission’s intensified efforts, including mandatory registration for Data Controllers and Processors, represent positive steps toward stronger oversight. However, as the outlook predicts, 2025 will see “stricter regulatory scrutiny, with steeper penalties for non-compliance.”
The Technology Integration Challenge
Nigeria’s e-governance framework must account for emerging technologies that present both opportunities and risks. Internet of Things (IoT) devices, increasingly integrated into government operations, are viewed by 80% of cybersecurity experts as highly vulnerable to attacks. Simultaneously, 85% recognize artificial intelligence as crucial for enhancing threat detection capabilities.
This dual nature of emerging technologies requires a balanced approach. Nigeria should implement stringent security controls for IoT deployments while investing in AI-powered security solutions that can identify and respond to threats in real-time. Machine learning algorithms can analyze patterns across government networks to detect anomalous activities that might indicate security breaches.
Blockchain technology also offers potential for securing government data and ensuring transaction integrity. However, implementation must be carefully managed to avoid introducing new vulnerabilities while gaining the benefits of distributed ledger technology.
Practical Implementation Strategies
For Nigeria to successfully implement a holistic cybersecurity framework, several practical steps are essential:
Immediate Actions:
- Establish a centralized cybersecurity command center responsible for monitoring all government digital assets
- Implement mandatory multi-factor authentication across all government systems
- Begin systematic updates of legacy systems, starting with the most critical and vulnerable components
Medium-term Initiatives:
- Develop a national e-governance security standard that all agencies must adopt
- Create specialized cybersecurity training programs for government IT personnel
- Establish public-private partnerships to leverage private sector expertise in cybersecurity
Long-term Strategic Goals:
- Build indigenous cybersecurity capabilities through education and research investments
- Develop a robust incident response network that can handle national-scale cyber emergencies
- Create citizen awareness programs that promote digital literacy and security best practices
The Economic Imperative
The economic case for robust e-governance cybersecurity is compelling. Cyber attacks on government systems can cost millions in direct damages, but the indirect costs—including lost citizen trust, reduced foreign investment, and compromised national security—are far greater. Research indicates that organizations with comprehensive cybersecurity frameworks experience 23% fewer security incidents and 27% lower incident response costs.
Moreover, secure e-governance systems enable more efficient service delivery, reducing bureaucratic costs and improving citizen satisfaction. Estonia’s digital government initiatives, protected by robust security measures, have generated estimated savings of 2% of GDP annually through improved efficiency and reduced administrative overhead.
Building Citizen Trust Through Transparency
Successful e-governance security requires more than technical measures—it demands citizen confidence in the system. Currently, privacy loss is identified as the primary factor undermining e-government credibility globally. Nigeria must address this through transparent data handling practices, clear privacy policies and regular security audits that are publicly reported.
Agencies should educate citizens to help them understand how their data is protected and the mechanisms available to them to report security concerns. This transparency, combined with demonstrably secure systems, will drive adoption rates and maximize the benefits of digital government services.
The Insurance Safety Net
The 2025 outlook identifies cybersecurity insurance as “the new lifeline” for organizations facing escalating cyber risks. While historically underutilized in Nigeria, these specialized policies provide crucial financial protection against incidents like data breaches, ransomware attacks, and third-party liabilities.
For government agencies, cyber insurance is a risk management tool that can incentivize better security practices and provide resources for rapid recovery from incidents. However, challenges such as high premiums, limited local expertise and skepticism about coverage details may hinder adoption in the public sector.
Regardless, the question is not whether Nigeria can afford to implement comprehensive cybersecurity measures for its e-governance systems, but whether it can afford not to. The cost of inaction when measured in compromised citizen data, disrupted services and lost trust, far exceeds the investment required to build a secure digital government infrastructure.
